Event-Driven Icons: Linking User Behavior to Modern Cybersecurity Solutions
Understanding Event-Driven Icons in Cybersecurity
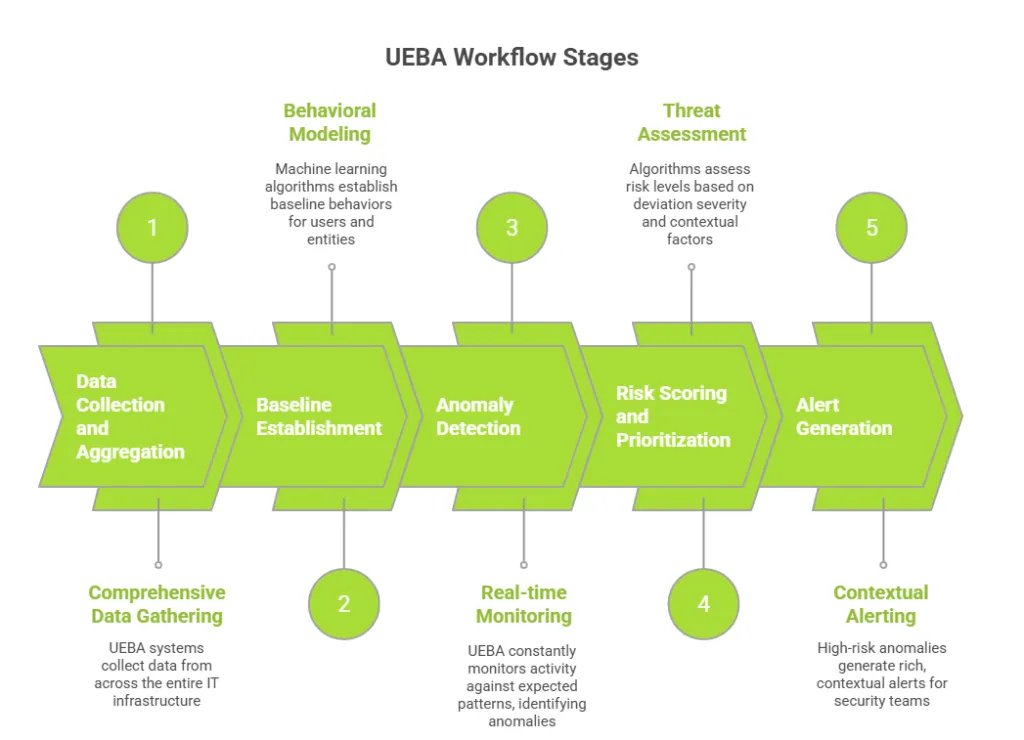
Event-driven icons represent key actions taken by users within a digital environment. These icons are essential for capturing user behavior data that helps identify potential security threats. By analyzing how users interact with these icons, organizations can glean valuable insights into their cybersecurity posture.
The Importance of Linking User Behavior to Cybersecurity
Linking user behavior to cybersecurity strategies is increasingly crucial as cyber threats evolve in complexity and sophistication. Monitoring event-driven icons allows security teams to proactively address vulnerabilities and respond to incidents more effectively.
- Enhanced Security Posture: Organizations can strengthen their defenses by understanding the normal behavior associated with event-driven icons.
- Proactive Threat Detection: Patterns in user interaction with these icons can signal potential breaches or malicious activity.
Conclusion: A Necessity in Modern Cybersecurity
In a landscape where traditional security measures fall short, integrating user behavior analytics with cybersecurity frameworks through event-driven icons is no longer optional—it's essential for protecting data integrity.
This article was prepared using information from open sources in accordance with the principles of Ethical Policy. The editorial team is not responsible for absolute accuracy, as it relies on data from the sources referenced.